Before You Begin: Review Azure Billing Account Types
Microsoft offers different billing account types based on your organization’s setup. The way that you’ll complete your Azure integration with Vantage depends on which account type you have. If your organization uses a Microsoft Customer Agreement (MCA), Enterprise Agreement (EA), or Azure Cloud Solution Provider (CSP), follow the specific integration steps linked below. If you are on another account type such as Pay as You Go, use the instructions on this page to integrate your account with Vantage.Microsoft Customer Agreement (MCA)
Follow the specific integration steps for Microsoft Customer Agreement (MCA) accounts.
Enterprise Agreement (EA)
Follow the specific integration steps for Enterprise Agreement (EA) accounts.
Azure Cloud Solution Provider (CSP)
Follow the specific integration steps for Azure Cloud Solution Provider (CSP) accounts.
Azure GovCloud
Azure Government Cloud requires additional manual configuration by the Vantage team. Customers cannot currently enable this through the UI. If you need to connect an Azure Government Cloud subscription, contact Vantage Support and provide the following information after integrating:- Your Azure Government Cloud tenant ID
- The billing account ID associated with the GovCloud tenant (
/providers/Microsoft.Billing/billingAccounts/<billing_account_id>). Note: Subscription-based GovCloud accounts may not have a billing account ID.
Connect Your Azure Account (Non-MCA, EA, or CSP Account)
This service principal is assigned access to individual subscriptions.The service principal is granted Reader permissions. It does not have permissions—nor will it ever attempt—to make any changes to your infrastructure.
Connect via the Azure CLI
Prerequisites
- You must have a Vantage Organization Owner or Integration Owner role to add or remove this integration. See the Role-Based Access Control documentation for details.
- The below commands are run via the Azure CLI. Ensure you have access to Azure CLI and can create service principals and manage their permissions.
- Create a free Vantage account, then follow the steps below to integrate Azure costs.
Step 1 - Create an Azure Service Principal
Create a service principal using the following command:appId, password, and tenant as you will enter these credentials into the Vantage console.
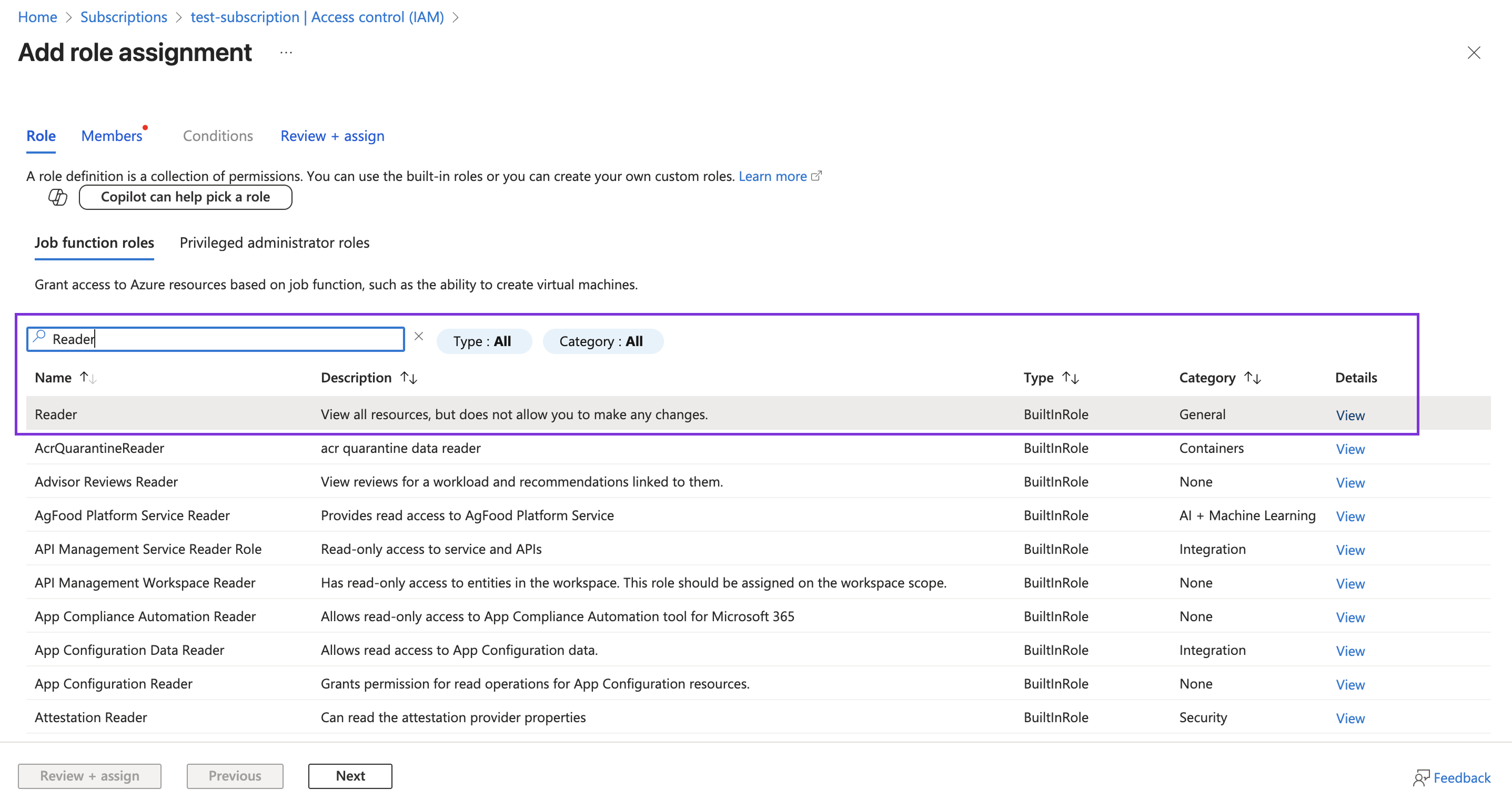
Step 2 - Grant the Service Principal Permissions
Grant permissions to theappId from the service principal created above. The scope is a subscription. Ensure you replace <SERVICE_PRINCIPAL_APP_ID> with the appId. Replace <SUBSCRIPTION_ID> with your subscription ID.
Connect via the Azure Portal
Prerequisites
- You must have a Vantage Organization Owner or Integration Owner role to add or remove this integration. See the Role-Based Access Control documentation for details.
- The below instructions are for connecting using the Azure portal. If you already completed the steps via the Azure CLI, skip to the Save the Credentials in Vantage section. You should have access to set up service principals and grant those service principals permissions.
- Create a free Vantage account, then follow the steps below to integrate Azure costs.
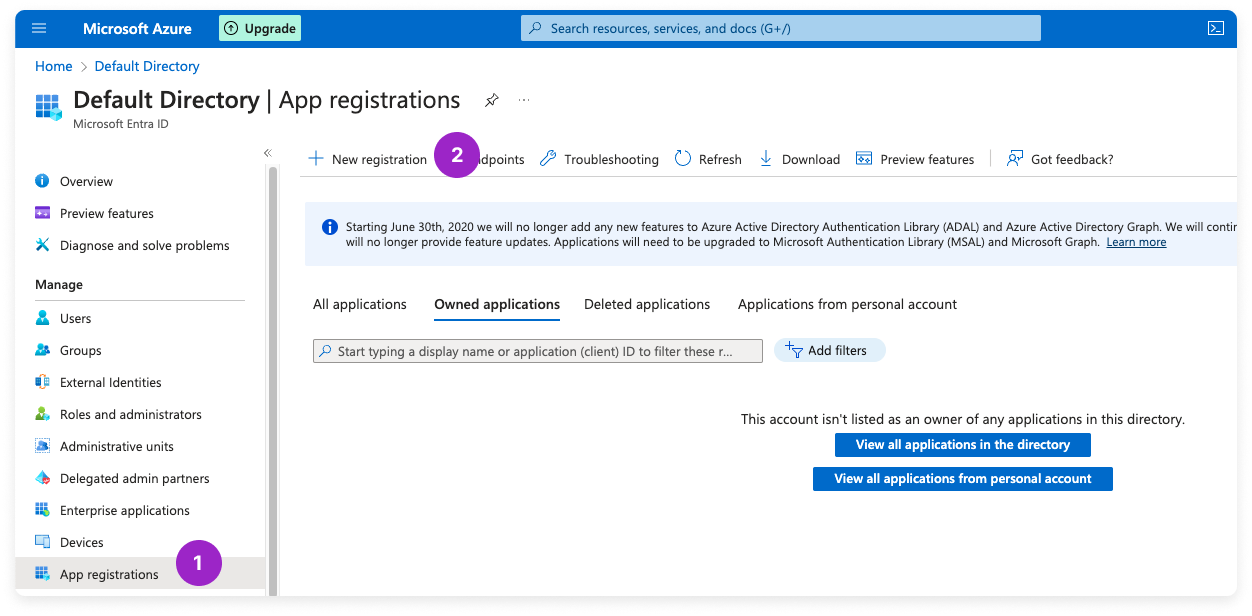
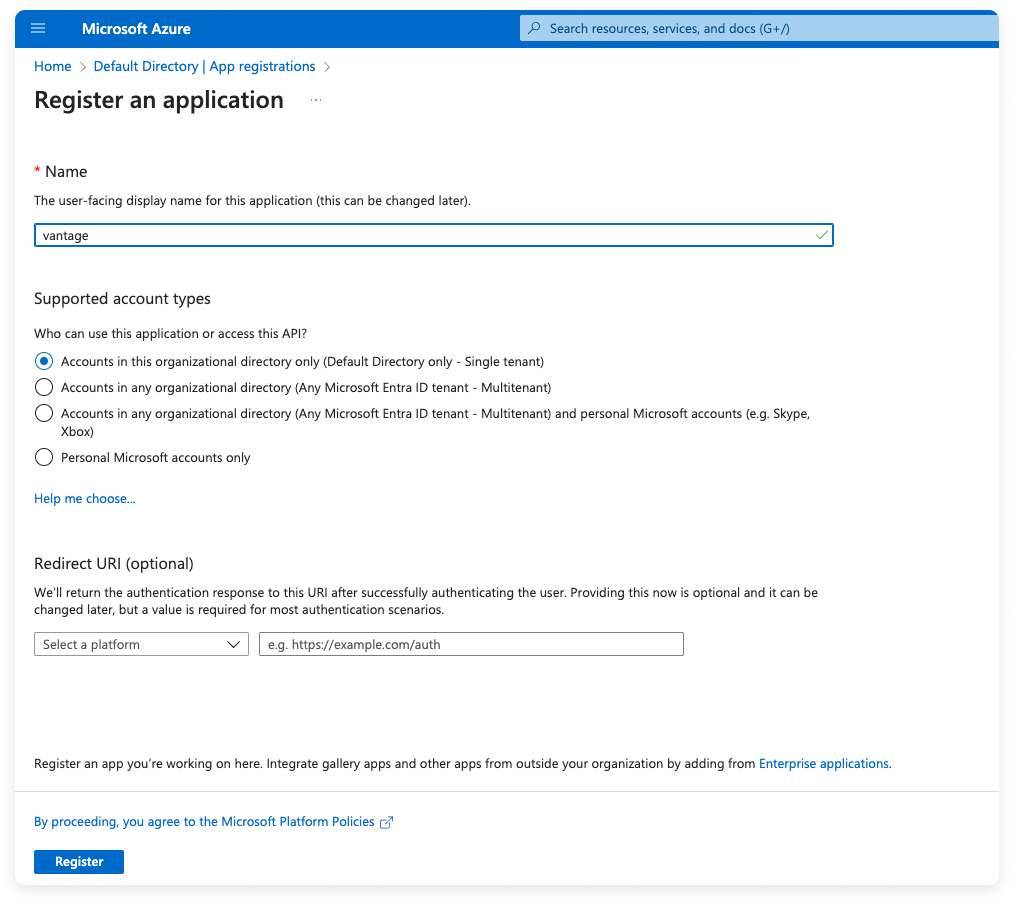
Step 1 - Create a New Application Registration
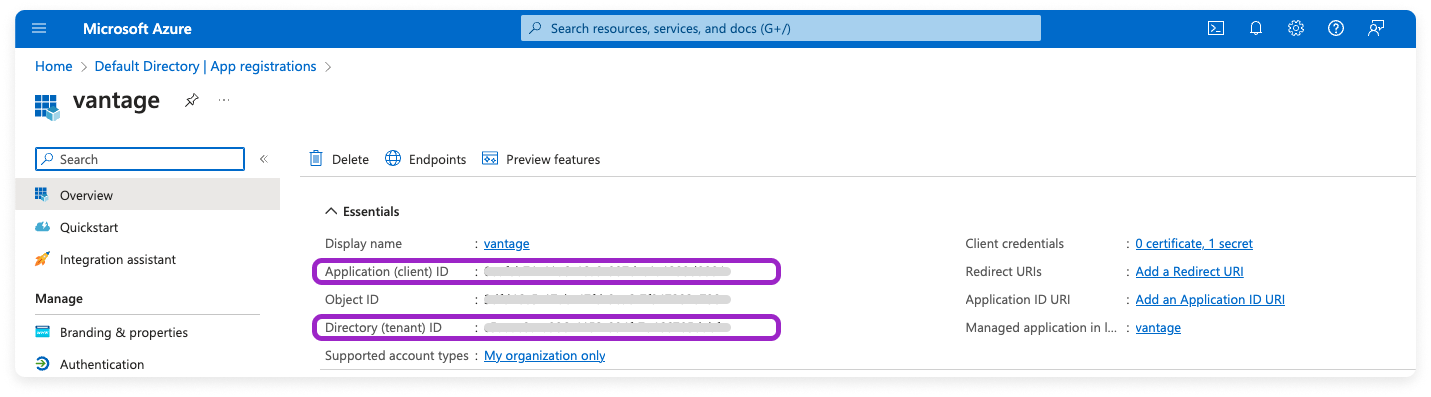
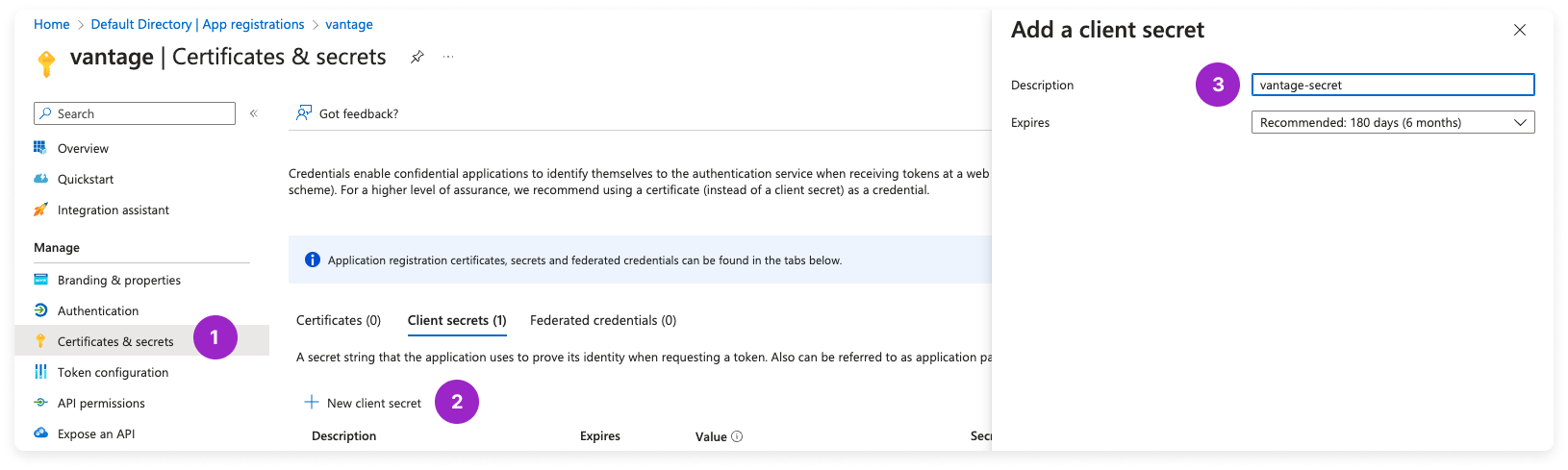
Step 2 - Generate a Client Secret
On the same page, next to the Client credentials field, click Add a certificate or secret. (You can also access the Certificates and secrets screen from the left navigation menu.)
The Add a client secret pane is displayed. For Description, enter a description, such as vantage-secret.
Click to view example image
Click to view example image

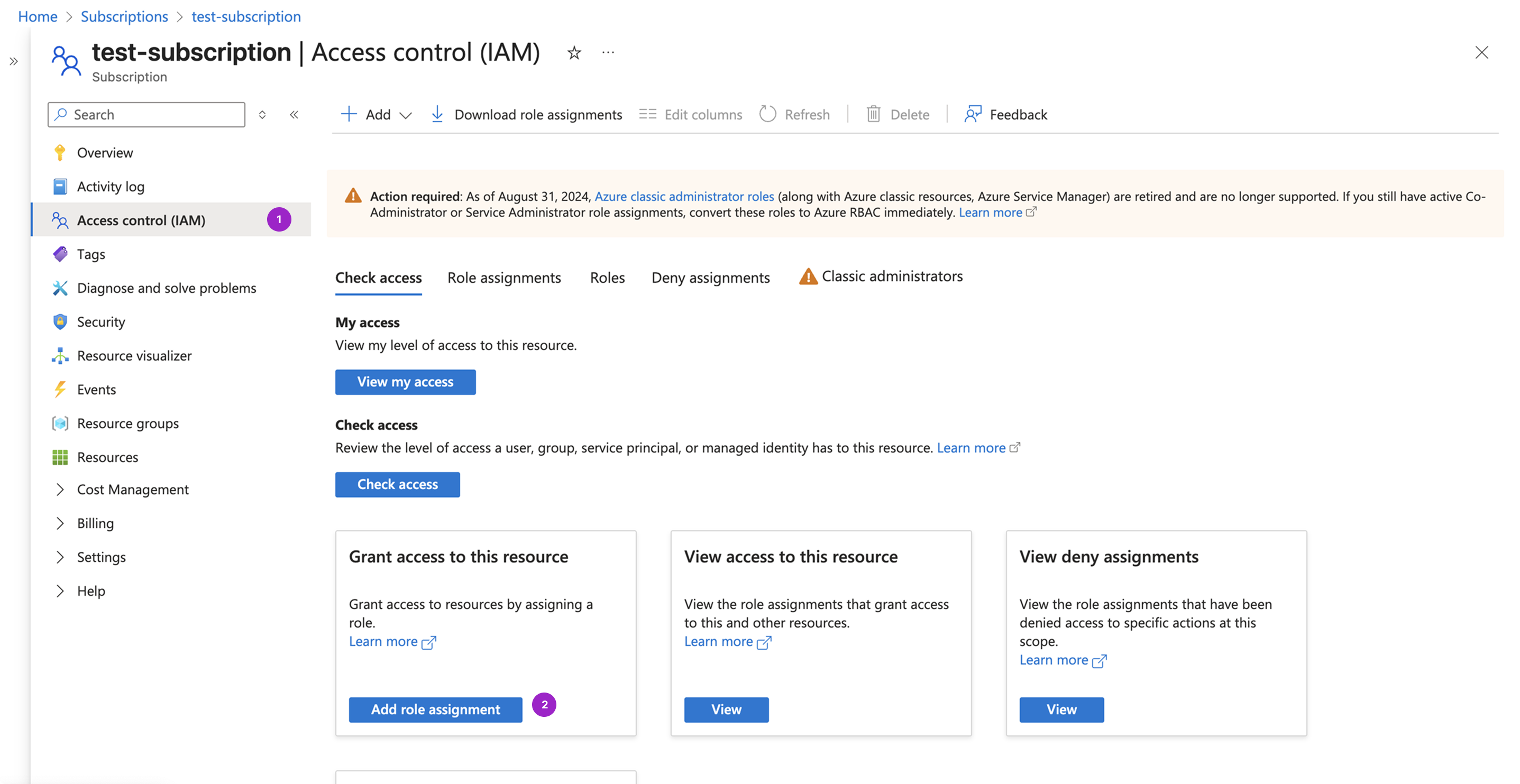
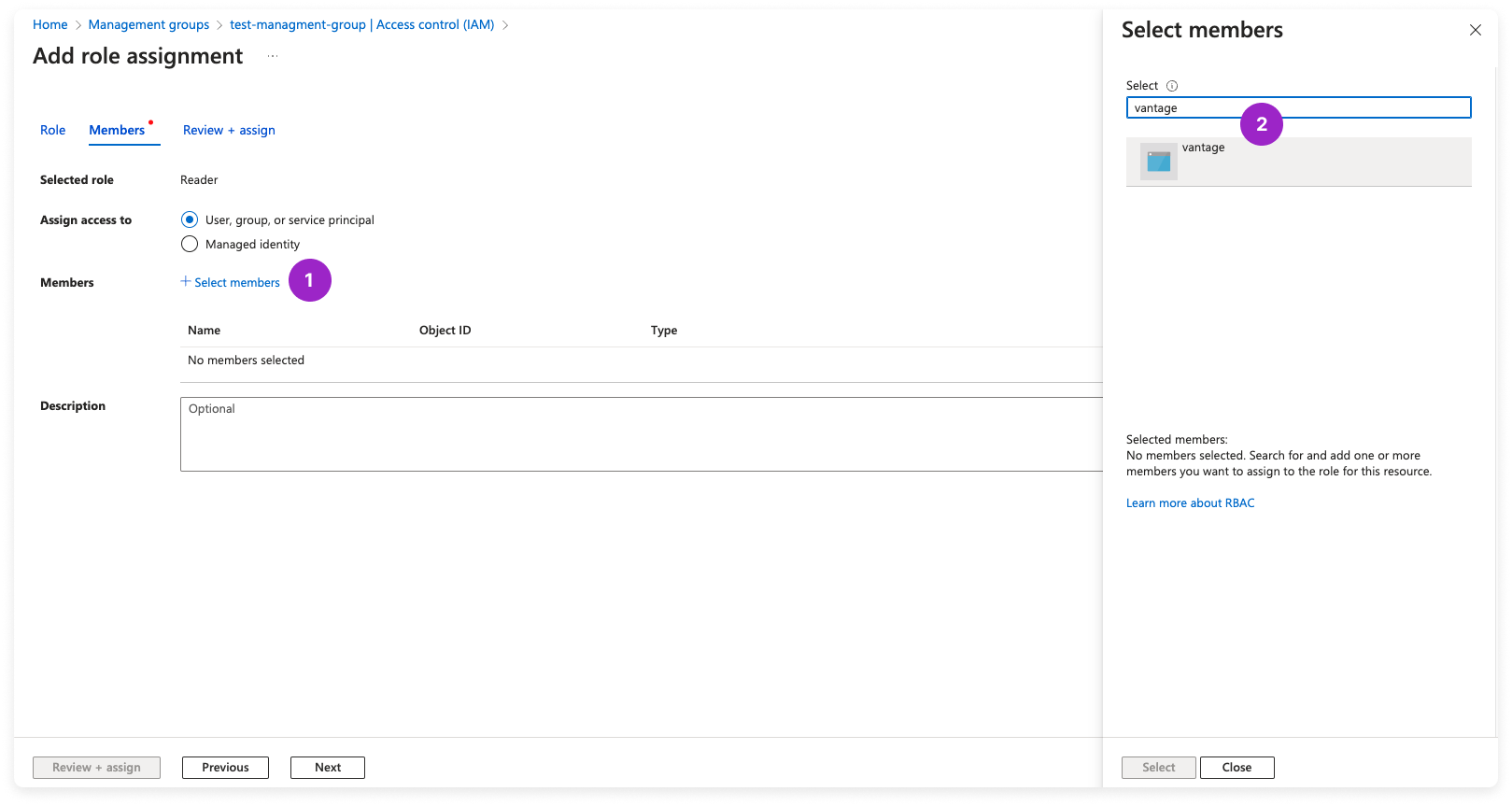
Step 3 - Grant the Service Principal Permissions
Click + Select members. The Select members tab is displayed on the right. Search for the vantage app you created before. Select the listed app, then click Select.
Click to view example image
Click to view example image

Save the Credentials in Vantage
After you complete the steps for connecting via the Azure CLI or Azure portal, follow the steps below to add the Azure tenant ID, service principal App ID, and service principal password/secret in Vantage.Navigate to the Integrations page in the Vantage console, and add an Azure integration.
Next Steps - Manage Workspace Access
Once the import is complete and the integration status changes to Stable, you can select which workspaces this integration is associated with. See the Workspaces documentation for information.Update Your Client Secret
If you need to update your Azure integration’s client secret, you can do so from the individual Manage Connection integration page in Vantage.Navigate to the Azure Integrations page.
Contact support@vantage.sh to request that your integration data be reimported with the new credentials.
Data Refresh
See the provider data refresh documentation for information on when data for each provider refreshes in Vantage.Azure Amortization
Azure stores their actual and amortized billing data in separate tables. Vantage pulls in both tables for you to view either costs types within Cost Reports, with no additional integration steps required. To switch between actual and amortized costs, select Settings at the top of any Cost Report, and check or uncheck the Enabled checkbox in the Amortization section.Azure does not show unused reservations within their amortized views. If performing charge back for Azure cost data, ensure you use either actual costs or use Custom Providers to add in unused reservation costs to your amortized Azure views.
Azure Cost Recommendations
Vantage provides different cost recommendations for Azure. Each recommendation includes a potential monthly savings value, which is something that is not shown in Azure Advisor. Savings estimates are displayed in USD.Kubernetes and AKS
Vantage supports Kubernetes cost allocation on Azure, including Kubernetes clusters running on VMs or through AKS. Vantage recommends using the Vantage Kubernetes agent to monitor and ingest Kubernetes costs from Azure.Azure Reporting Dimensions
On Azure Cost Reports, you can filter across several dimensions:- Resource Group (resource group name)
- Category (e.g., Virtual Network IP Addresses)
- Tag/Not Tagged (includes Azure tags and virtual tags created in Vantage for this provider). In addition, the following provider tags are automatically created by Vantage from Azure data and are available for filtering and grouping:
azure:costCenter: The cost center value from Azure billing data, allowing you to filter and group costs by cost center.azure:resourceGroup: The resource group name associated with the cost, allowing you to filter and group costs by resource group. Use the separate Resource Group dimension for the full name.azure:InvoiceSectionId: The invoice section ID when present in the source data, allowing you to filter and group costs by invoice section.azure:InvoiceSectionName: The invoice section name when present in the source data, allowing you to filter and group costs by invoice section.
- Subcategory (e.g., Virtual Network Standard IPv4 Static Public IP)
- Resource (resource ID)
- Region (e.g., Us East)
- Charge Type (e.g., Usage)
- Subscription (subscription name)
- Marketplace (Toggle to show only Marketplace purchases or excluded)
- Service (e.g., Virtual Machines)